As a continuation of our blog post on Securing Web Applications, here are the top 10 most critical security risks for web applications and their probable solutions. The Open Web Application Security Project (OWASP) is a non-profit organization whose goal is to raise awareness about application security. The OWASP Top 10 is referenced by many standards, books, tools, and organizations, including MITRE, PCI DSS and many more.
The ten 10 most critical web application security risks are :
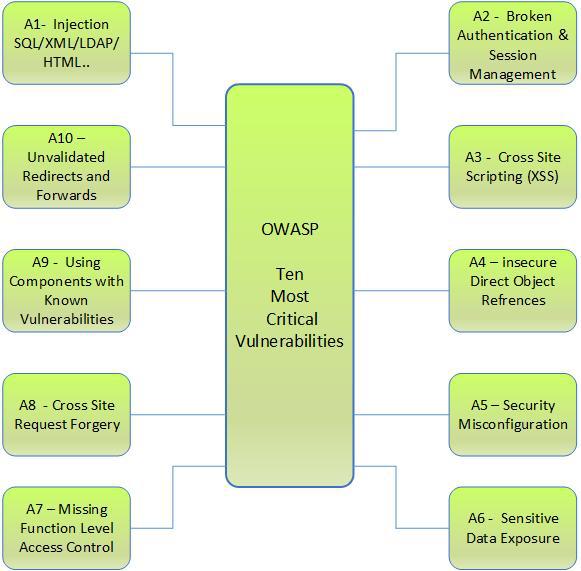
Let us try to understand the most common threats to a web application.
A1: Injection
Problem
Issue occurs when user input is sent to an interpreter as a part of a command or a query without encoding or validation. There are different types of Injections i.e. SQL, LDAP, XPath, XSLT, HTML, XML and OS command.
Solution
Use safe APIs, such as strongly typed parameterized queries and object relational mapping (ORM) libraries. Avoid providing detailed error messages. Validate input data for length, type and syntax.
A2: Broken Authentication and Session Management
Problem
This vulnerability occurs when authentication and session management functions are not implemented correctly. Attacker can completely bypass these functions and gain the unauthorized access to the system.
Solution
Use of session expiration and login expiration is encouraged. Avoid predictable login credentials. Invalidate the session value after logout. Avoid session ID to be used in application url. User credentials should be protected when stored in database. Enable encryption of sensitive information.
A3: Cross Site Scripting (XSS)
Problem
Reflected XSS occurs when a page reflects user provided data back to user. Stored XSS occurs when hostile data could be stored in a file or a database and at later stage displayed back without filtering.
Solution
Output encoding should be implemented on both the client and server side. Server-Side input validation should be done. White-listing of incoming data should be performed.
A4: Insecure Direct Object Reference (IDOR)
Problem
IDOR vulnerability occurs when authentication levels of system are not sufficiently checked and users gain administrative access to system data. By taking the advantage of this system flaw, attacker can modify the object references to access the unauthorized data.
Solution
For each user, request to direct reference object must perform the access control check, to ensure that the user is authorized for the requested object. Also it’s a good idea to have a code analysis and evaluation performed to determine any potential authentication holes where an unauthorized user can slip through and gain access.
A5: Security Misconfiguration
Problem
This issue occurs due to improper server or web application configuration which may lead to flaws like incorrect folder permission, keeping default accounts and passwords, which can provide easy access to system.
Solution
Updating software with latest fixes and patches will help. Running scans and doing audits periodically to help detect future misconfigurations or missing patches is recommended.
A6: Sensitive Data Exposure
Problem
This occurs when data in transport is not encrypted (Passing data in clear text). The data can vary and anything from passwords, session tokens, credit card data to private health data and more can be exposed.
Solution
Data between database and server, or over the internet should not be in clear text. Don’t store sensitive data unnecessarily. Discard it as soon as possible. Ensure strong standard algorithms and strong keys are used, and proper key management is in place.
A7: Missing function level access control
Problem
This vulnerability exists in case of websites with hierarchical or tier level user access accounts. When the user requests any function, the server should check the user access control to that particular function. If request is not verified on server side, the attacker will be able to make a forge request in order to access functionality for which he has no permission.
Solution
The authentication mechanism should deny all access by default, and provide access to specific roles for every function. Access control lists (ACL) and role-based authentication mechanisms should be implemented.
A8: Cross-Site Request Forgery (CSRF)
Problem
CSRF occurs when a malicious website, email, blog, instant message or a program causes a user’s web browser to perform an unwanted action on a trusted site, for which the user is currently authenticated. The attacker’s vulnerable application generates the request in victim’s browser, so that it looks like valid request to the victim and performs the action for that.
Solution
To prevent CSRF, use unpredictable token in each HTTP request. Token should be unique per user session. Also can implement challenge-response.
A9: Using Components with Known Vulnerabilities
Problem
Normally applications use a large number of third-party, open source libraries and software. Vulnerabilities in these third-party libraries and software is used by an attacker to compromise the security of systems using the software.
Solution
Identification of all components and the versions that are being used in the web apps is needed. Add security wrappers around such components which are vulnerable by nature.
Always try to use latest versions of the libraries and frameworks. Perform regular security tests.
A10: Unvalidated Redirects and Forwards
Problem
Web applications frequently redirect and forward users to other pages and websites. This
issue occurs when a web application accepts untrusted input that could cause the web application to redirect the request to untrusted website. Attackers can redirect victims to malicious sites, or use forwards to access unauthorized pages.
Solution
Notification to users before redirect and forward is first step. All input must be validated against a white-list of acceptable value ranges.